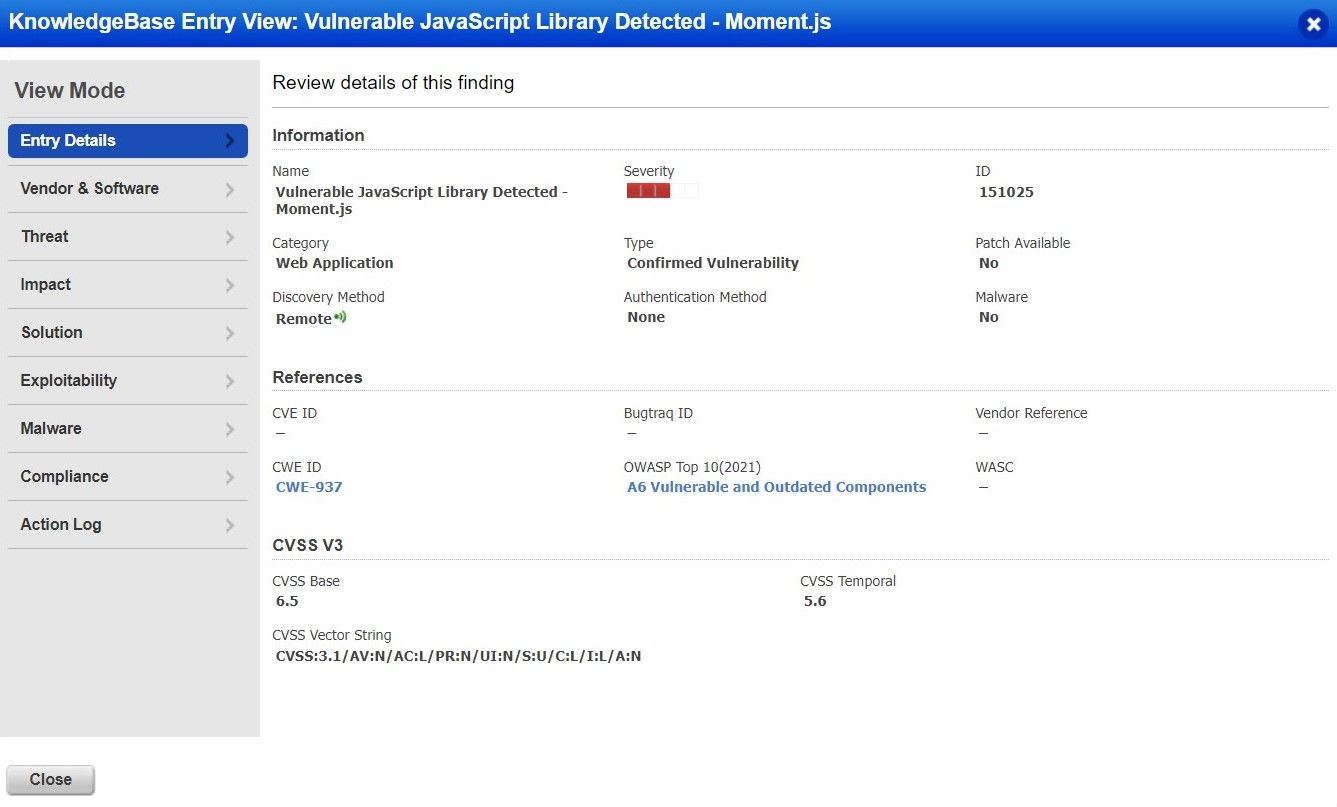
CVE-2022-24785 (High) detected in moment-2.29.1.tgz · Issue #1432 · opensearch-project/OpenSearch-Dashboards · GitHub

Writing Exploits for Win32 Systems from Scratch | NCC Group Research Blog | Making the world safer and more secure

Information | Free Full-Text | Exploitation of Vulnerabilities: A Topic-Based Machine Learning Framework for Explaining and Predicting Exploitation